HTB Anti Flag Reversing
Table of Contents
Anti Flag
This file is part of the track “Intro to Reversing”. Because this file does not give any HTB points at the time of this writing, i will keep the flag inside the post.
The file is a 64 bit elf binary:
localhost:~# file anti_flag
anti_flag: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=b8de97bc12c627606510140e43fc13e2efffcee5, for GNU/Linux 3.2.0, stripped
As the strings output is very short it can also be pasted here and it is obviosu that there are not many strings included:
/lib64/ld-linux-x86-64.so.2
libc.so.6
puts
__stack_chk_fail
strlen
malloc
ptrace
__cxa_finalize
__libc_start_main
GLIBC_2.4
GLIBC_2.2.5
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
u+UH
[]A\A]A^A_
2asdf-012=14
#*HK
Well done!!
No flag for you :(
:*3$"
GCC: (Ubuntu 9.2.1-9ubuntu2) 9.2.1 20191008
.shstrtab
.interp
.note.gnu.property
.note.gnu.build-id
.note.ABI-tag
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.plt.got
.plt.sec
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.dynamic
.data
.bss
.comment
Executing the file returns a failed message.
localhost:~# ./anti_flag
No flag for you :(
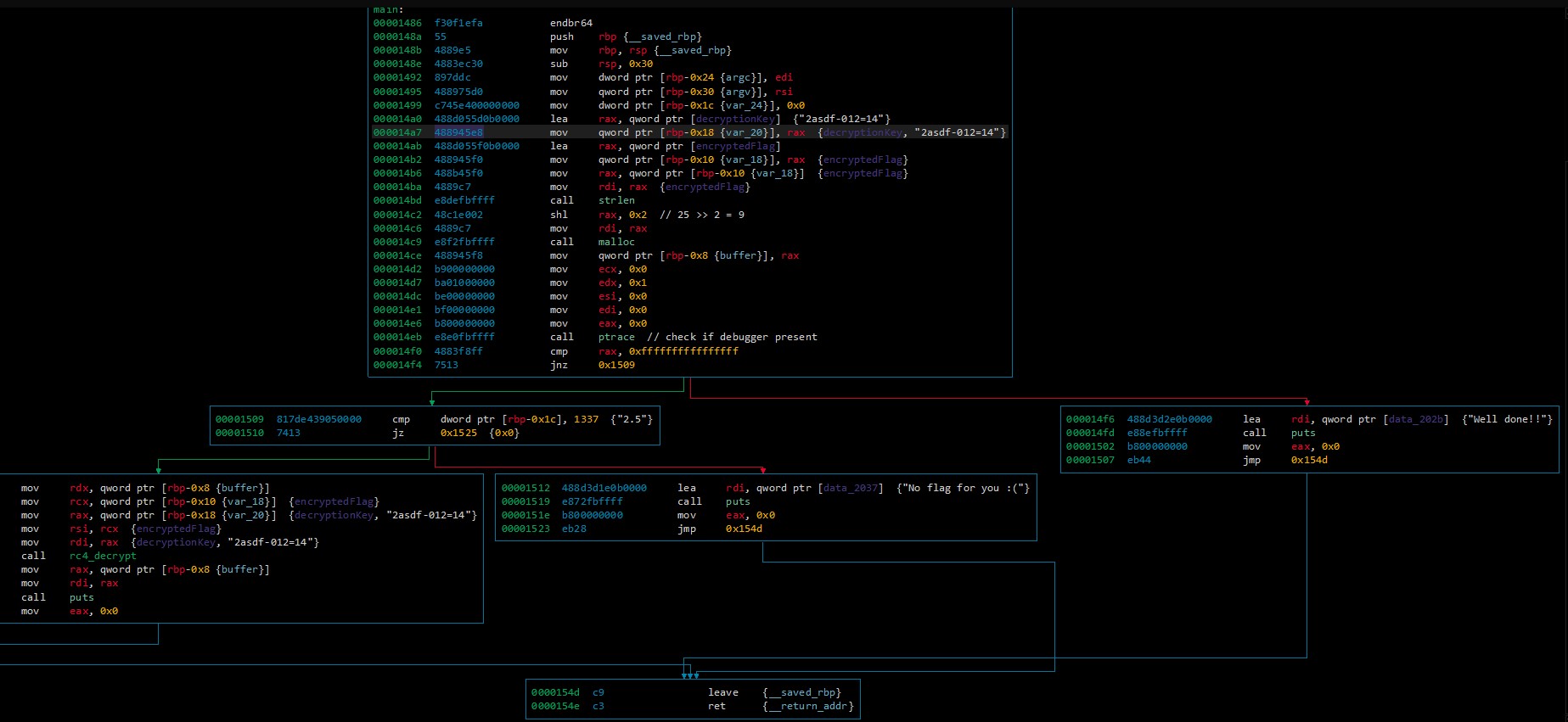
A look at the strings and a quick look at the disassembly shows that the file checks for the presence of a debugger:
000014ce 488945f8 mov qword ptr [rbp-0x8 {buffer}], rax
000014d2 b900000000 mov ecx, 0x0
000014d7 ba01000000 mov edx, 0x1
000014dc be00000000 mov esi, 0x0
000014e1 bf00000000 mov edi, 0x0
000014e6 b800000000 mov eax, 0x0
000014eb e8e0fbffff call ptrace // check if debugger present
If a debugger is detected a different message is printed.
localhost:~# ltrace ./anti_flag
Well done!!
+++ exited (status 0) +++
A total overview of the dissasembly with a few replaced names can be found in the screenshot.
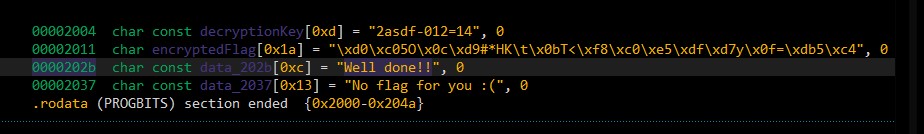
The relevant strings are defined at 0x2004 and 0x2011:
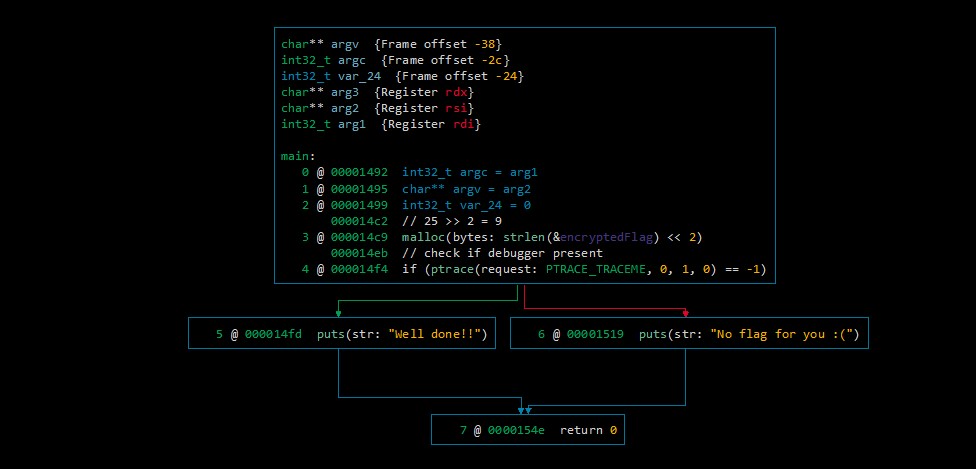
The following shows a high level intermediate language view of the main function:
Comparing this to the disassembly, it becomes clear that the basic block from 0x1525 to 0x154d is not represented in the representation. The reason for this is, that the block is unreachable.
At address 0x1499 the variable is set to 0, this variable is later on compared to reach the decryption code
00001499 mov dword ptr [rbp-0x1c {alwaysFalse}], 0x0
However the variable is never modifed before reaching this comparison, therefore it will always fail.
00001509 cmp dword ptr [rbp-0x1c], 1337
This always false value is shown clearly in the MLIL interpretation via the comparison
11 @ 00001510 if (false) then 15 @ 0x1525 else 22 @ 0x1519
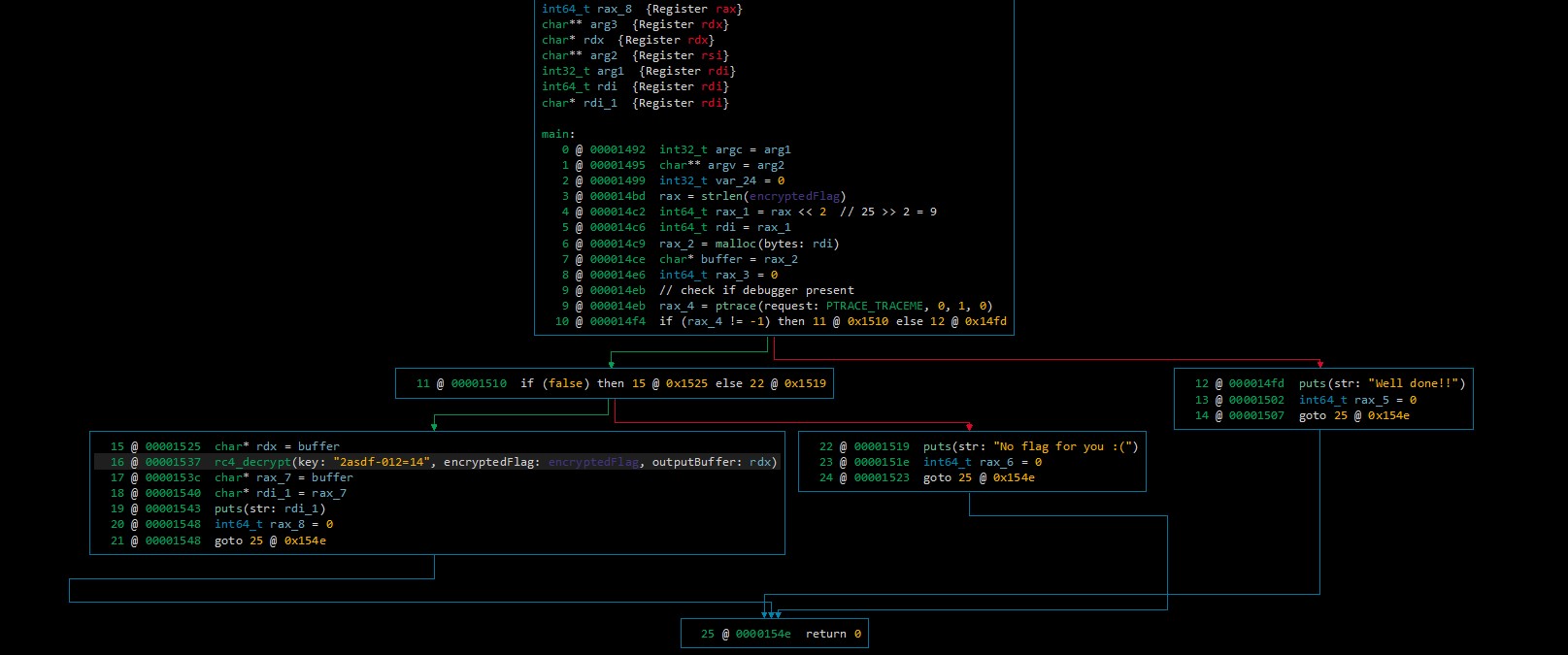
Therefore, it is currently not possible for the original program to reach the decryption code.
This problem can be solved in two ways to get to the flag value. It is possible to either patch the binary to reach the decryption code, or it is possible to decrypt the data.
Patching
It is possible to ignore the ptrace command and the secondary comparisson with the “1337”/false value by patching the jump at address 0x14f4 from
000014f4 7513 jnz 0x1509
to
jmp 0x1525
In Binary Ninja this works by selecting the instruction, pressing “e” and just writing the new asm. Afterwards the file can be saved via “Save as” and save file contents.
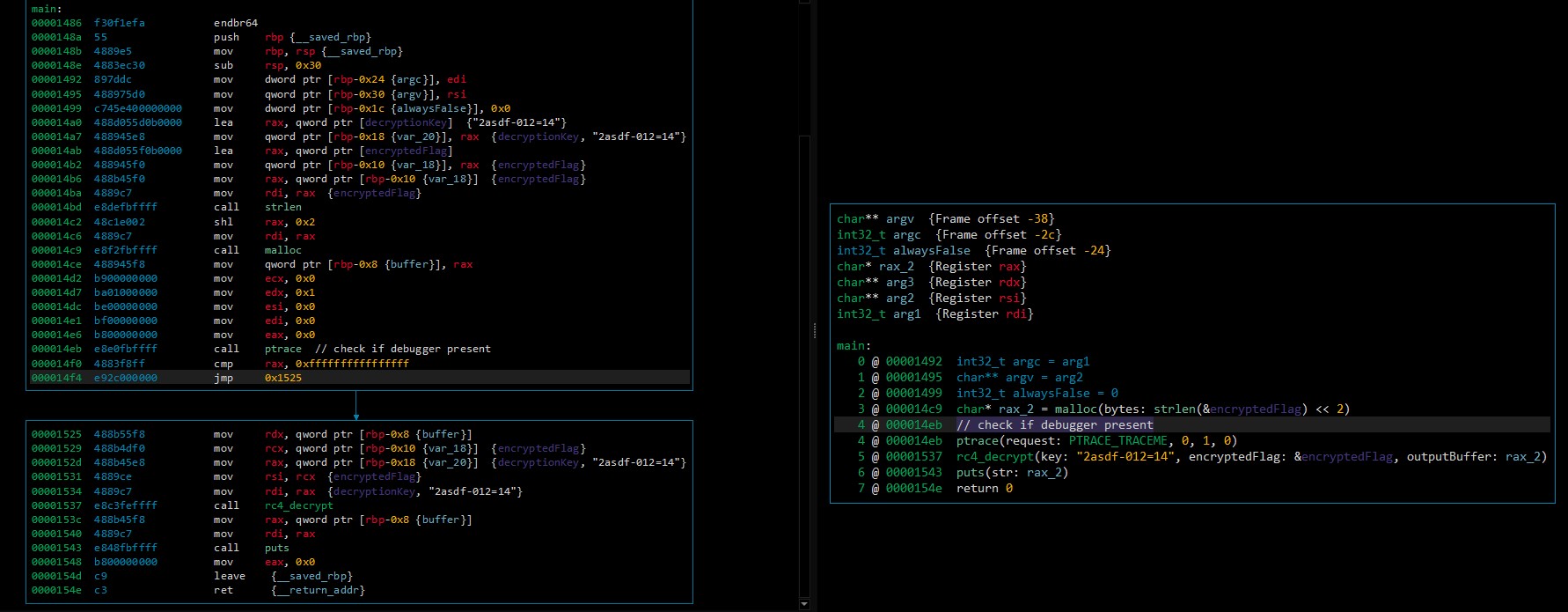
Like this the code of the decryption will always be executed:
ot@localhost:~# chmod +x anti_flag_patch
ot@localhost:~# ./anti_flag_patch
HTB{y0u_trac3_m3_g00d!!!}
Decrypting
After some investigation it becomes clear that the call at 0x1537 is a call to decrypt RC4 data. Therefore we can either use the Binary Ninja builtin RC4 transformation or we copy the data to Cyberchef.
To use the RC4 transformation we need to undefine the variable first (or switch to hexview), after that we can select the entire flag data and use the RC4 tranformation (right click, transform, rc4).
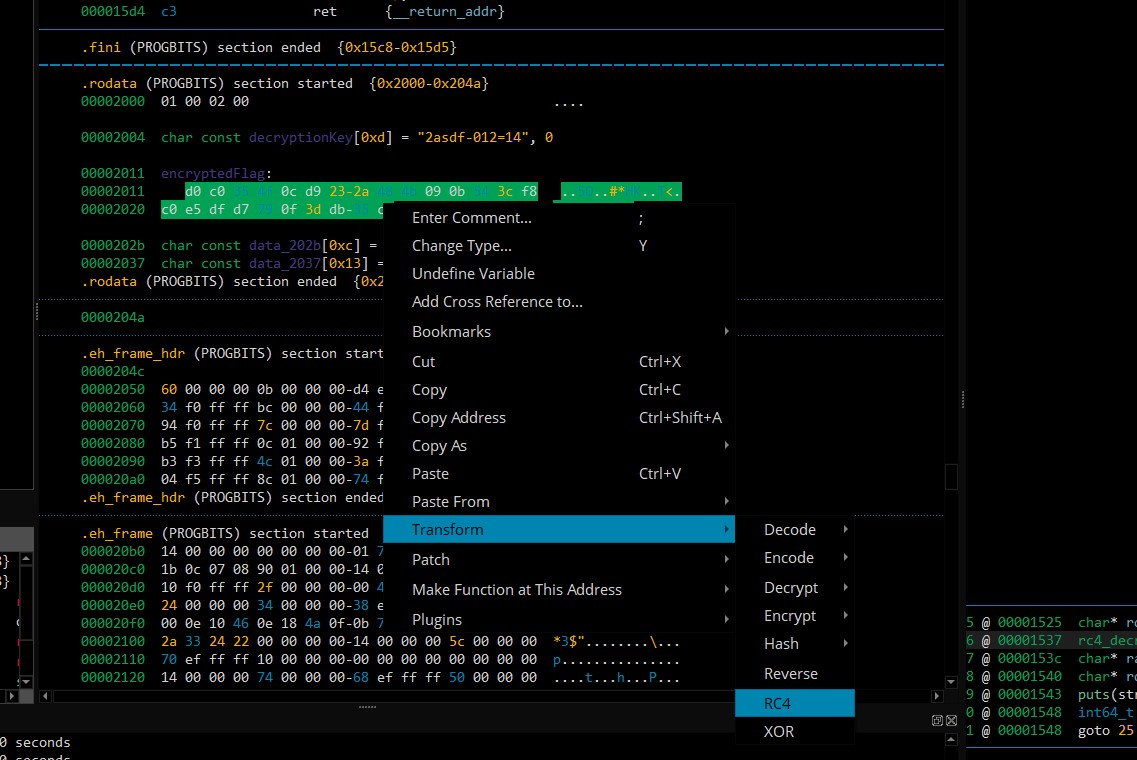
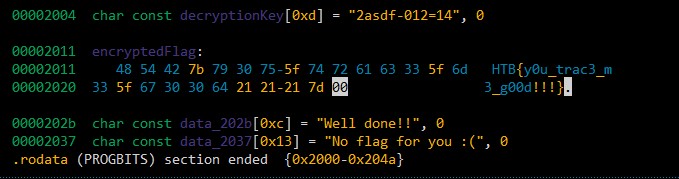
The raw hex at address 0x2011 is the RC4 encrypted flag data
d0c0354f0cd9232a484b090b543cf8c0e5dfd7790f3ddb35c4 so the entirety of the data needs to be selected and the used key is: 2asdf-012=14 (The transformation asks for the key after clicking the RC4 button). And the result of the decryption will be shown in the binary.
Another way of decrypting is to copy the hex bytes to cyberchef and using the RC4 decryption.
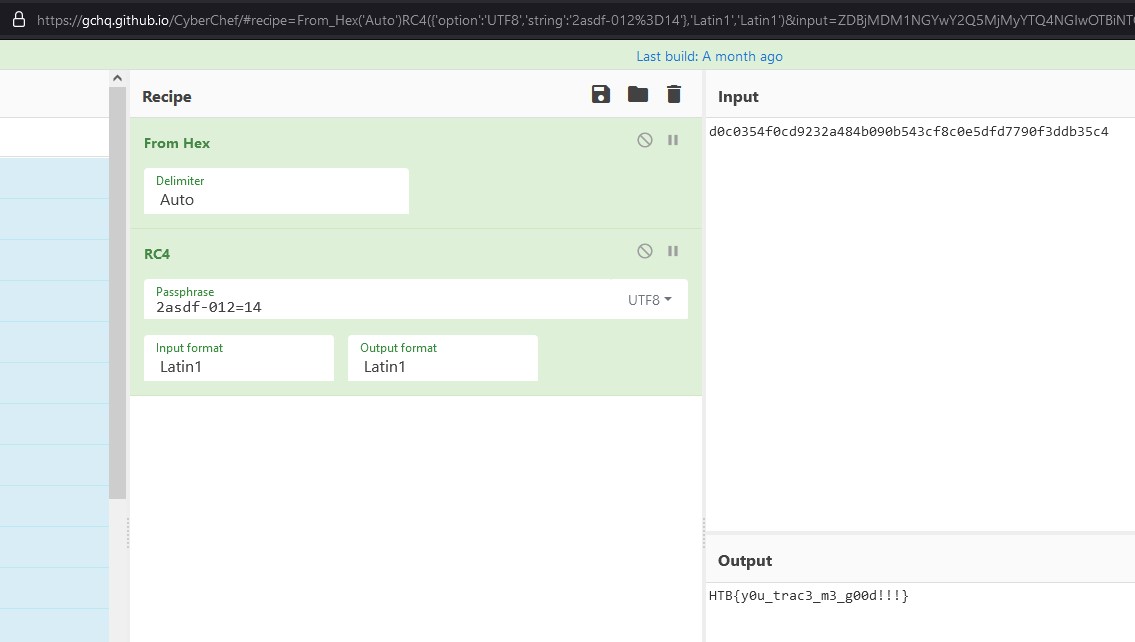
Flag
HTB{y0u_trac3_m3_g00d!!!}