Basic Malware RE THM room
Table of Contents
Basic Malware RE
This is a quick writeup of the basic malware re room from tryhackme found at https://tryhackme.com/room/basicmalwarere. The room contains 3 challenges in which the user has to find the flag that is used to calculate the displayed MD5 hash. In this post all challenges are solved without running the executables, only static analysis is used.
strings 1
Description
This executable prints an MD5 Hash on the screen when executed. Can you grab the exact flag?
Solution
The file contains a large number of fake flags which are visible when running the strings command.
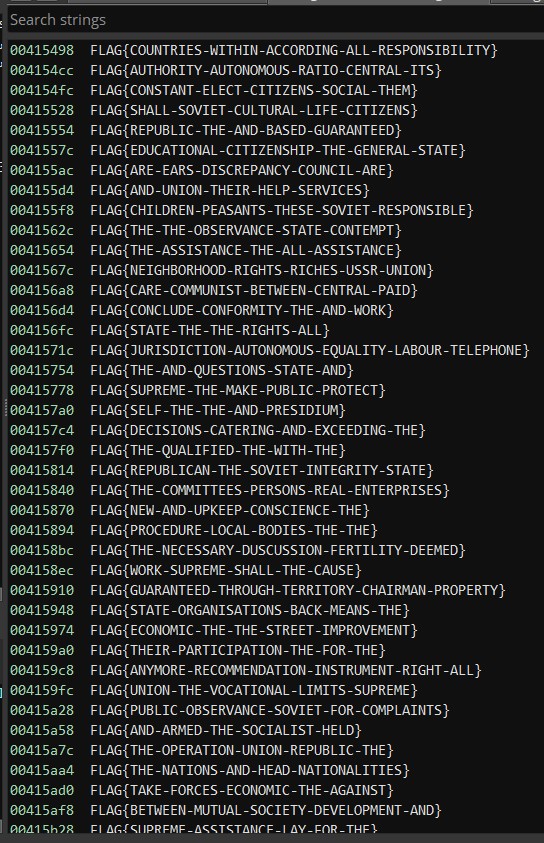
It could be possible to calculate the MD5 for all flags, including fake and real flags, however this seems a lot of overkill and analyzing the program is faster for this.
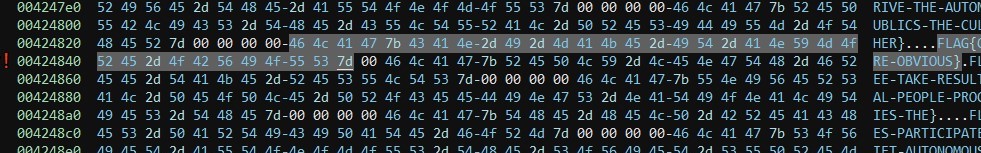
Looking at the function at 0x4022b0 shows the flag being passed to the md5_hash function.
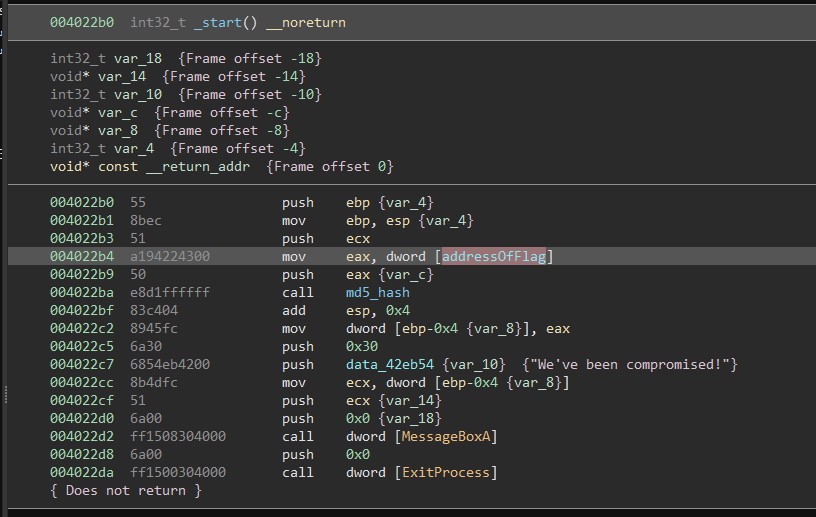
The high level il view for the function looks like this
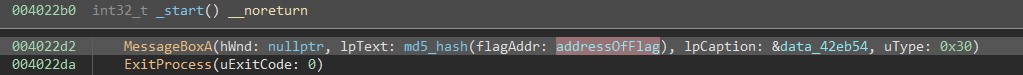
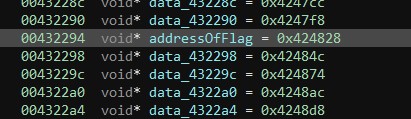
Following the address in the disassembler leads to the flag.
strings 2
Description
This executable prints an MD5 Hash on the screen when executed. Can you grab the exact flag?
Solution
The file calculates the MD5 of a string, this string is created on the stack and it is also the flag we search.
It should be no problem to run this in the debugger and look at the stack to see which string is passed into the MD5 calculation function. However another way is to look check the string building in the disassembler.
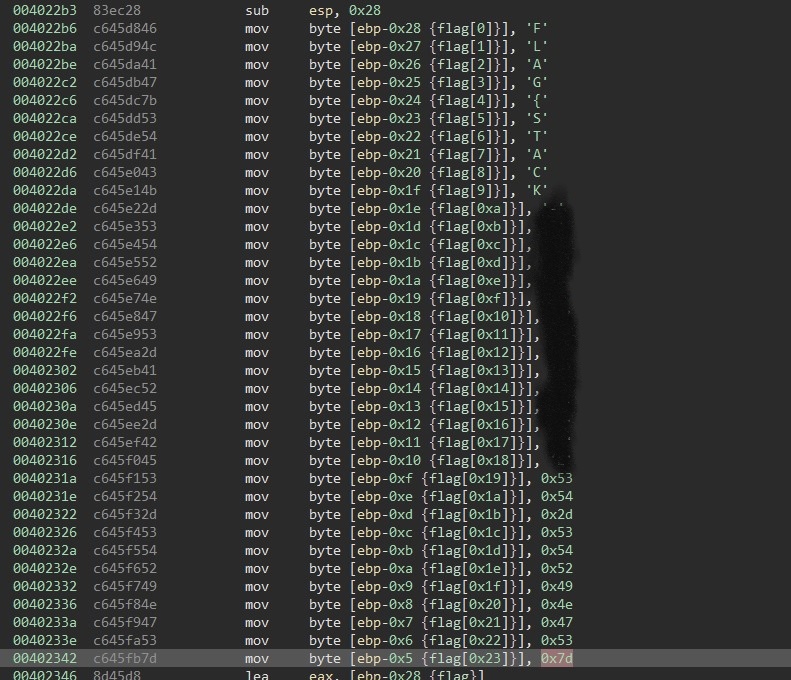
As the string is a bit longer, i created a small python script to run in the binary ninja snippet editor. This script comments on a selected section of code and writes the current string into the comments of the instructions (however there is no error handling or similar).
bv.begin_undo_actions()
r = current_selection
start = r[0]
end = r[1]
current = start
current_comment = ""
while current < end:
current_const_src = current_function.get_low_level_il_at(current).src
current_comment = current_comment + chr(current_const_src.constant)
bv.set_comment_at(current,current_comment)
current = current + bv.get_instruction_length(current)
bv.commit_undo_actions()

strings 3
Description
This executable prints an MD5 Hash on the screen when executed. Can you grab the exact flag?
Solution
In this challenge LoadStringA is used, this function loads a string from the resource section.
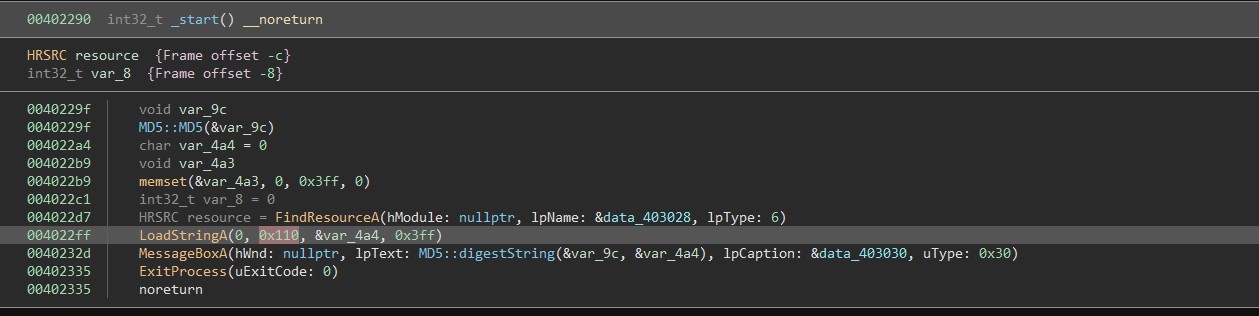
As can be seen in the above screenshot resource 0x110 (272 decimal) is loaded from the resources and for that string the MD5 is calculated. Opening the excutable in ghidra one can scroll to the resource section / select it in the GUI.
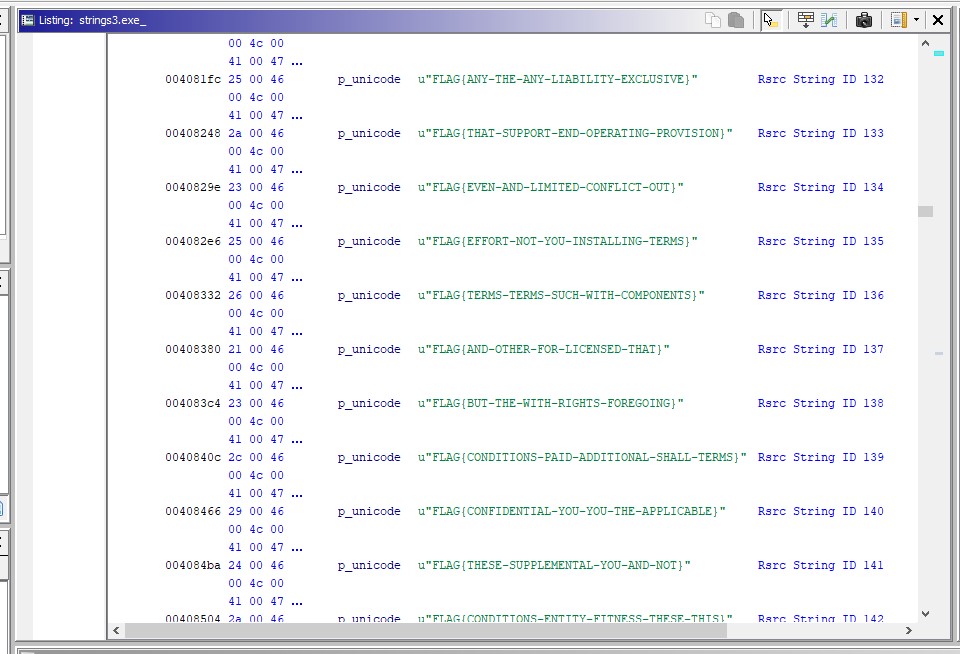
Now we only need to scroll until the right hand side reads: “Rsrc String ID 272” and we have found the flag.